Suggested Articles:
TCP - UDP Protocol Analysis
UDP Protocol - Header
This article covers the UDP protocol. We examine the structure of the UDP header, the protocols that use UDP as a transport plus a lot more.
Some ...
Domain Name System (DNS)
The DNS Protocol - Part 1: Introduction
If you ever wondered where DNS came from, this is your chance to find out ! The quick summary on DNS's history will also help you understand why DN...
Network Cabling
Early Communication Technology - Morse Code and...
We tend to think of digital communication as a new idea but in 1844 a man called Samuel Morse sent a message 37 miles from Washington D.C. to Balti...

Network Fundamentals
DoS & DDoS Attacks
A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a website, server or network by flooding it with traff...
Featured Subcategories:
Netflow Articles:
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
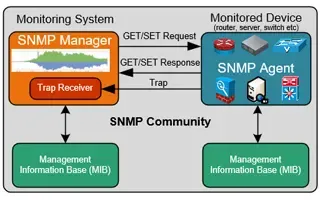
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
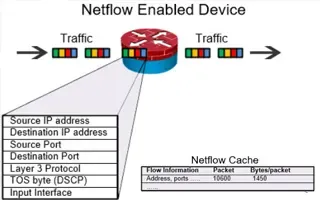
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...
Your IP address:
3.144.222.208
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q...

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative over...

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and secur...

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of...
Routing
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Pro...
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll exami...
Routing
Hybrid Routing Protocols - Advantages and Disadvanta...
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scala...
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informa...
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the...
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Backup Ad...
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to move...
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colasoft's ...
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network prob...
SASE & SD-WAN Networks
WAN Optimization vs SD WAN Networks. Today’s Challen...
Enterprises have been successfully running WAN optimization appliances at their many distributed sites for years. The devices have done a good job of he...
Cisco Routers
Configuring Cisco Dynamic Multipoint VPN (DMVPN) - H...
Our DMVPN Introduction article covered the DMVPN concept and deployment designs. We explained how DMVPN combines a number of technologies that give it i...




















