Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Dynamic NAT - Part 2
| Read |
|
Articles:
Dynamic NAT - Part 1
| Read |
|
Articles:
Static NAT - Part 2
| Read |
|
Articles:
Static NAT - Part 1
| Read |
|
Articles:
The Network Address Translation Table
| Read |
| Read | |
Suggested Articles:

Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 1: Understand STP...
One of the most used terms in network is LAN (Local Area Network). It’s a form of network that we encounter in our daily lives, at home, at work, s...
IP Protocol
IP Protocol - Part 2: The Internet Protocol (IP...
This article examines the Internet Protocol (IP) and its position within the OSI Model. We take a look at the IP Header and all fields contained wi...
Supernetting & CIDR
Supernetting In-Depth Analysis - Learn to Ident...
Our previous article served as an introduction to Supernetting, also known as Route Summarization. We covered the concept of Supernetting, how it w...
The OSI Model
The OSI Model: Layer 1 - Physical Layer
The Physical layer has two responsibilities: it sends bits and receives bits. Bits come only in values of 1 or 0. The Physical layer communicates d...
Featured Subcategories:
Netflow Articles:
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
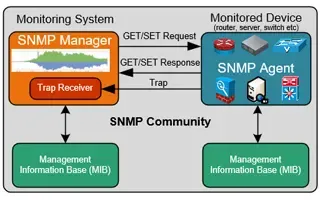
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...
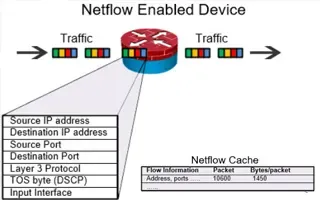
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
Your IP address:
18.224.63.87
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
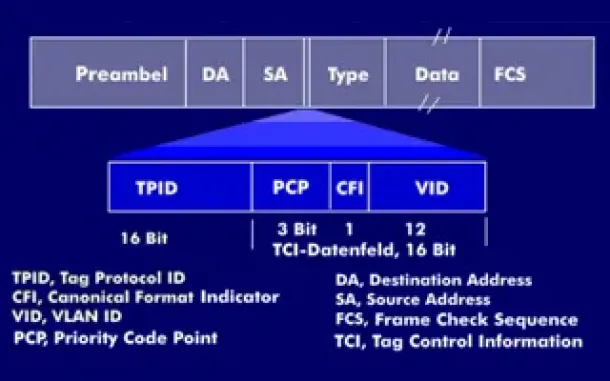
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently ...

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trun...

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and secur...

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of...
Routing
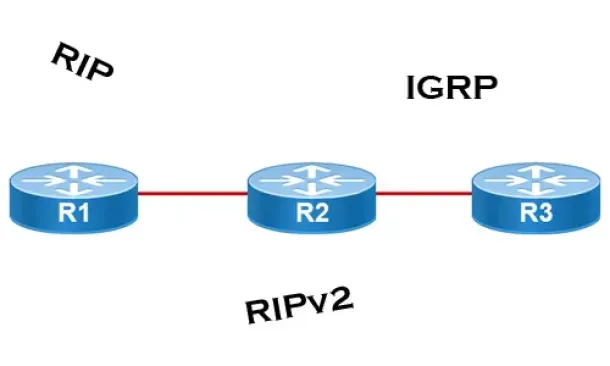
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their inte...
Routing
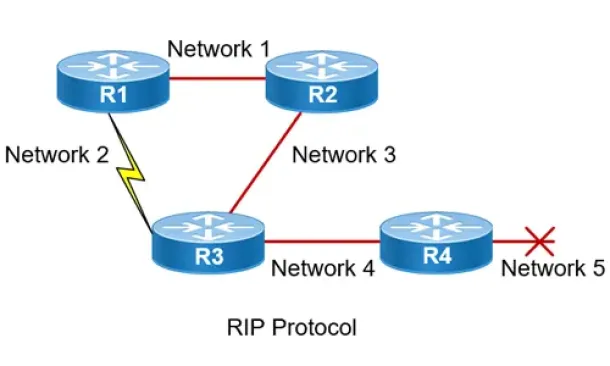
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the...
Routing
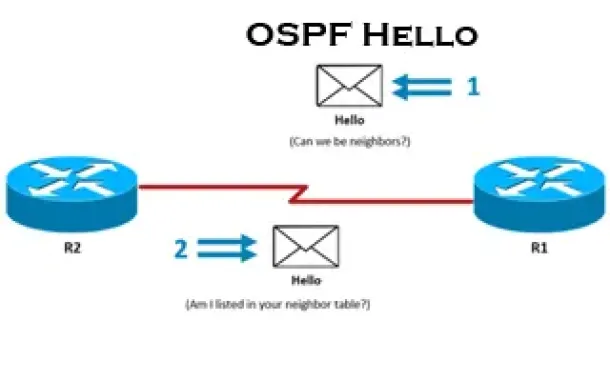
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Pro...
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll exami...
Routing
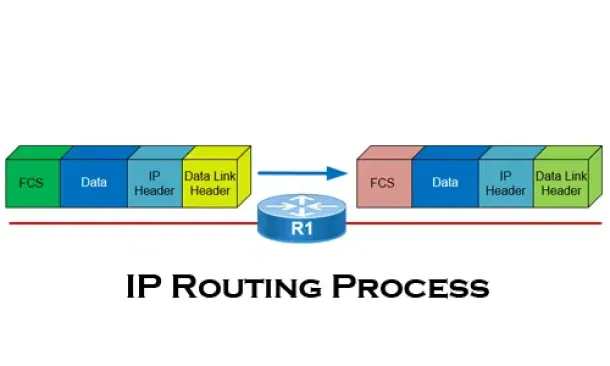
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all yo...
Cisco Routers
Configuring Static Route Tracking using IP SLA (Basic)
In today's network environment, redundancy is one of the most important aspects, whether its on the LAN side or on the WAN side. In this topic we will b...

Windows Servers
Deploying Active Directory & DNS Services on Windows...
This article provides a comprehensive guide to deploying Active Directory and DNS Services on Windows Server 2022, encompassing the Essential, Standard,...
Cisco Firewalls
Cisco ASA 5500 Series Firewall Modules & Cards – Con...
Cisco’s Adaptive Security Appliance (ASA) Firewalls are one of the most popular and proven security solutions in the industry. Since the introduction of...
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration from a...




















