Network Fundamentals: Top Picks
Network Fundamentals
Need for Speed – The Data Tsunami & Advancement...
A long-long time ago (not long ago in earth time) 100 Mbps was THE technology. 100 Mbps uplinks bundled with ether-channel was the ultimate uplink ...
Network Fundamentals
Power over Ethernet - Understanding PoE Technol...
Power over Ethernet (PoE) was invented by PowerDsine back in 1997 and the first power injector (Midspan) was installed in 1998! Many manufacturespa...
Network Fundamentals
Introduction to Content Switching - Application...
Content switches (also sometimes called application switches) is a class of network device that is becoming increasingly common in medium to large ...
Network Fundamentals
Introduction To Networking
A network is simply a group of two or more Personal Computers linked together. Many types of networks exist, but the most common types of networks ...
Featured Subcategories:
Netflow Articles:
Netflow
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...
Netflow
Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
Netflow
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
Netflow
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...
Network Protocols:
Supernetting & CIDR
What is Supernetting (Route Summarization) & Ho...
Supernetting is the opposite of of subnetting, and is also known as route aggregation or CIDR (Classless Inter-Domain Routing). Supernetting is a t...
Domain Name System (DNS)
The DNS Protocol - Part 4: DNS Response Message...
The previous article covered the DNS Query message formats. In the article we analysed them in great detail and showed how various options are sele...
Subnetting
IP Subnet Calculator
This free online Subnet Calculator provides a fast and easy way to calculate all aspects of any IP Address and Subnet Mask. Simply enter your des...
TCP - UDP Protocol Analysis
Transmission Control Protocol - Part 4: In-Dept...
This article is an introduction to the 7-page TCP Header analysis section that follows. We briefly view each section of the TCP Header and then mov...
Supernetting & CIDR
The Supernetting / CIDR Chart
This articles build upon our previous pages covering what is Supernetting (Route Summarization) & How Supernets Work and Supernetting In-...
Subnetting
IP Subnetting - Part 4: Routing Between Subnets
Routing and Communication between subnets is the main topic here. This article analyses communications between subnets. We provide examples on diff...
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 6: TCP Options
The TCP Options (MSS, Window Scaling, Selective Acknowledgements, Timestamps, Nop) are located at the end of the TCP Header which is also why they ...
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 3: TCP Header Len...
The third field under close examination is the TCP Header length. There really isn't that much to say about the Header length other than to explain...
STP/ICMP Protocols:

Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 3: Bridge ID, Pri...
In this article we will examine the Spanning Tree Bridge ID structure, explain why it has increments of 4096, how VLAN information is embedded (for...
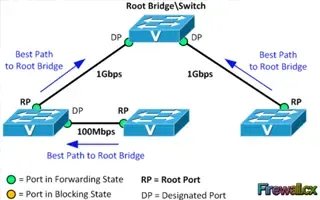
Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 2: Rapid STP Port...
Spanning Tree Protocol, Rapid STP port costs and port states are an essential part of the STP algorithm that affect how STP decides to forward or b...
ICMP Protocol
ICMP Protocol - Part 5: Source Quench Message A...
The ICMP - Source Quench message is one that can be generated by either a gateway or host. You won't see any such message pop up on your workstatio...
ICMP Protocol
ICMP Protocol - Part 2: Echo / Echo Reply (Ping...
As mentioned in the previous page, an Echo is simply what we networking engineers call a 'ping'. The Echo Reply is, as most would guess, the ...
Your IP address:
3.19.61.115
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Ne...

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of...

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of thei...

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trun...
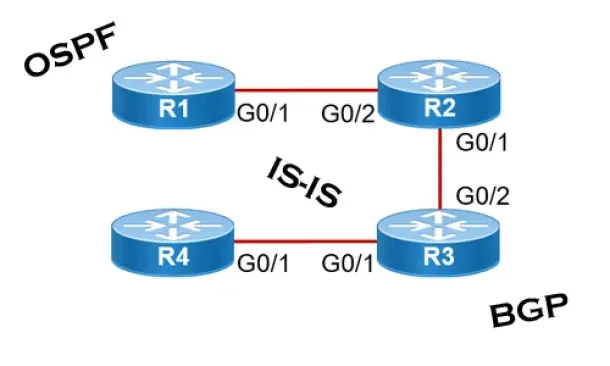
Routing
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall networ...
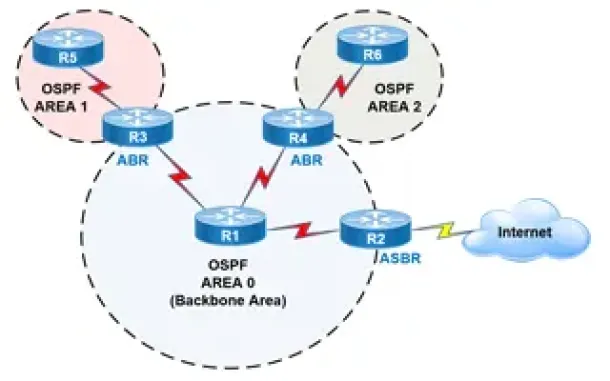
Routing
OSPF - Part 2: How OSPF Protocol Works & Basic Conce...
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose ...
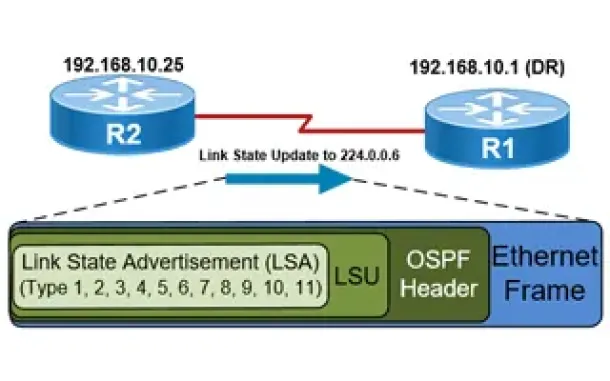
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (L...
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router rec...
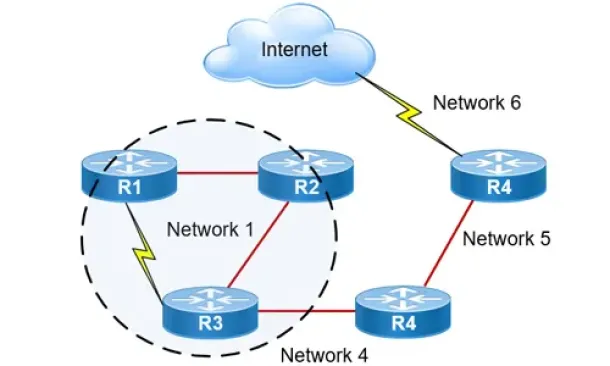
Routing
Hybrid Routing Protocols - Advantages and Disadvanta...
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scala...
Network Address Translation - NAT
Network Address Translation (NAT) Overload - Part 1
NAT Overload is the most common NAT method used throughout all networks that connect to the Internet. This is because of the way it functions and the li...
Network Address Translation - NAT
Dynamic NAT - Part 1
Dynamic NAT is the second NAT mode we're going to talk about. Dynamic NAT, like Static NAT, is not that common in smaller networks but you'll find it us...
Network Address Translation - NAT
The Network Address Translation Table
After that simple and informative introduction to the NAT concept, it's time to find out more about how it works and this is where the NAT table comes i...
Network Address Translation - NAT
Network Address Translation (NAT) Concepts
Before we dive into the deep waters of NAT, we need to make sure we understand exactly what NAT does. So let me give you the background of NAT, why it's...




















